SNMP Traps
With SNMP traps, you can reduce your network and server load and provide faster service to your customers.
ITRS acquires IP-Label. Read the press release.
With SNMP traps, you can reduce your network and server load and provide faster service to your customers.
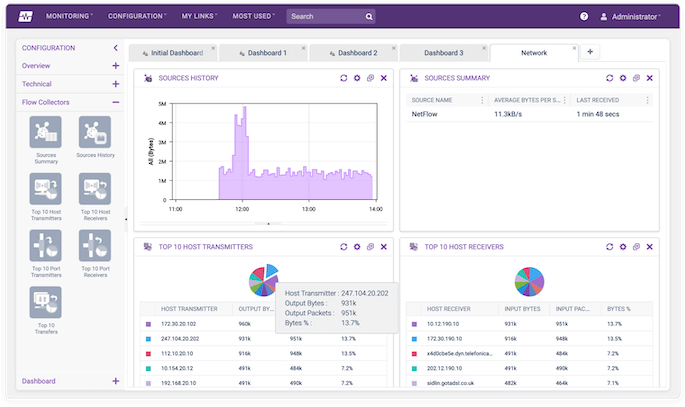
View real-time information for your network device activity. This is particularly useful on large networks as it can be used in place of active SNMP (where a device is polled for status information).
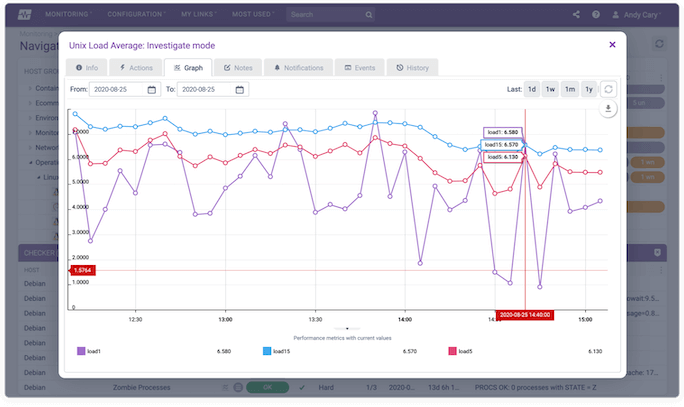
Devices can usually be configured to send specific types of trap such as link status changes, BGP, HSRP, and many others, making this a flexible monitoring option capable of running on 99.9% of network devices such as Cisco, Juniper, Dell, HP, and more.

Each Service Check configured to accept SNMP traps has an ordered list of rules. Each rule is evaluated in turn. If a rule is false, then the next rule is evaluated. If a rule matches as true, the specified action is taken and no more rules for that Service Check are evaluated.